The pandemic is accelerating the move to location-distributed work. Want to know how the rush into remote work has weakened the cybersecurity posture of companies? You can find plenty of proof on dark web marketplaces.
Threat actors have adjusted quickly to the "new normal". They are modifying their methods to profit from the changed environment.
That's what IT security firm Positive Technologies (PT) discovered when it looked at dark web marketplaces and found that the trade with corporate network logins and related information is booming.
In Q1 2020, when many companies moved to remote work, the number of dark web postings advertising access to corporate networks for sale jumped by 69 percent compared to the previous quarter.
The last quarter of 2019 had already seen rising figures, PT points out. The amount of large company network credentials for sale in Q4 2019 alone equaled the entire total of such listings observed in all of 2018.
The escalation seen in the first quarter of 2020 shows that attackers are now focusing on this particular approach.
One common way to carry out network-based attacks involves databases specifically set up to exploit stolen user credentials for networks on a large scale. The creators of such databases are letting others profit from their successful break-ins or data leaks they discovered.
One recent example was documented by Bleeping Computer (BC). The site reported in late May that it had been aware of a data breach broker selling an alleged database containing 40 million user records for the Wishbone app through private deals.
The same database had been released online two months earlier, in March, by the "Shiny Hunters" group, without charge. BC also reported that a different data breach seller publicly advertised the same database on a popular hacker forum for $8,000.
The Shiny Hunters have been associated with numerous other data breaches, including the exfiltration of 73.2 million user records from 11 different companies like Homechef, Minted, and Styleshare. Security researchers think the group was also behind the Tokopedia data breach, where 91 million user records were compromised and sold on hacking forums for $5,000.
The Unacademy breach, also attributed to the Shiny Hunters outlet, exposed the records of 22 million users. They were sold on darknet forums for $2,000. The prices charged on the black market for such credentials increased over the last quarter, which shows how their perceived value to other criminals has grown.
Previously on the Authentic8 blog, I have highlighted airport security threats. McAfee researchers showed in 2018 how an airport's networks could fall through the relatively simple use of RDP credentials provided by a darknet marketplace. The researchers analyzed the offerings of eight underground shops selling RDP access credentials to those willing to pay for them.
In fact, the security and building networks of one airport could be controlled through use of these RDP credentials. One of the sellers offered the credentials for as little as $10 per target. The McAfee researchers found that "[p]rices ranged from around US $3 for a simple configuration to $19 for a high-bandwidth system that offered access with administrator rights."
Similarly sensitive areas for which network access was sold on the dark web included government entities, health care institutions like hospitals or nursing homes, municipalities, housing associations, and more.
The pandemic has created a criminal gold rush online, fueled by wholesales of user data on dark web marketplaces. The business of black market data brokers is booming and based on a simple calculation: Why put in the effort to exploit your ill-gotten network access for uncertain gains in the future, if you can enrich yourself immediately by selling the "mining rights" to others and let them shoulder the risk?
Many CISOs and their teams are worried about attacks from external threat actors - and risk missing other dangers.
They overlook how some of the most massive credential dumps on the dark web happened because negligent IT teams badly configured an externally-facing database, turning it into a bubbling source of corporate network credentials to supply the dark markets. To cyber criminals, it makes no difference whether the data is stolen or served up unprotected to anyone who knows where to look.
Only a few years ago, access to such collections was limited to a chosen few who were careful whom they shared it with. Today, it's a commodity.
The niche was growing already before the pandemic. Now such credential sets are readily available en masse, peddled by specialized black marketeers. Others then front-load them into database-driven tools that automate large-scale ransomware attacks as-a-service, for a percentage of the profit.
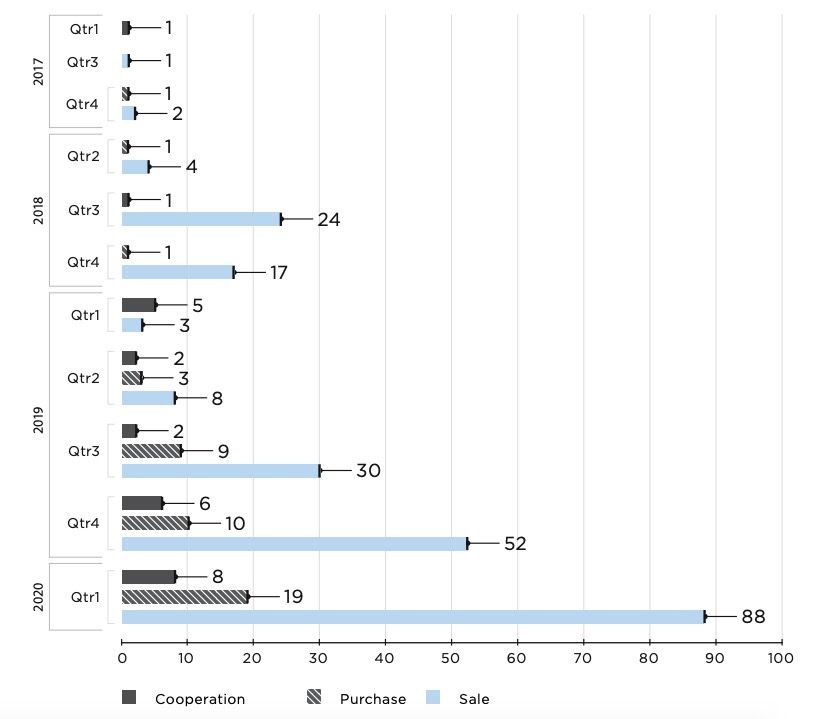
Source: https://www.ptsecurity.com/ww-en/analytics/access-for-sale-2020/
The military has a wide-ranging view of security prerequisites that it named CCIR – Commander's Critical Information Requirements. It is composed of three basic questions:
It is that last question that may not pop up in a routine IT security review, but it definitely should be included. The answer, following a thorough evaluation, may reveal a leaking data resource before it goes on sale on the dark web.
Does your company's IT security team have the means and procedures in place to face the dark web reality? Three essential steps you can take now:
New tools and security frameworks prove vital in this struggle. Increasingly, corporate security teams now deploy Silo for Research (Toolbox) for threat intelligence missions involving dark web investigations. It is also the research framework of choice for the Department of Defense, security-sensitive federal agencies, law enforcement, financial services providers, and major insurance firms, among others.
Silo for Research enables private sector organizations to conduct secure and anonymous research on the open and dark web. It protects their teams under adverse conditions and makes critical web research more efficient.
Silo for Research is built on Authentic8's Silo cloud browser, which uses web isolation to prevent exposure to web-borne exploits. Through its managed attribution capabilities, Silo for Research enables analysts to mask their online identity. Threat hunters can efficiently collaborate online using a wide range of tools, while risk and compliance managers maintain full visibility into the team members' online activities.
CISOs and CSOs in the private sector need to recast their organization's security posture to reflect the changed threatscape. Your business cannot afford to be the last one to learn about its digital assets going up for sale on the dark web.
This blog was authored by guest contributor Larry Loeb.
Larry Loeb has been online since uucp "bang" addressing (where the world existed relative to !decvax) and served as editor of the Macintosh Exchange on BIX and the VARBusiness Exchange. He wrote for BYTE magazine, was a senior editor for the launch of WebWeek, and authored books on the Secure Electronic Transaction Internet protocol and "Hack Proofing XML" (his latest). Larry currently writes about cybersecurity for Security Now.